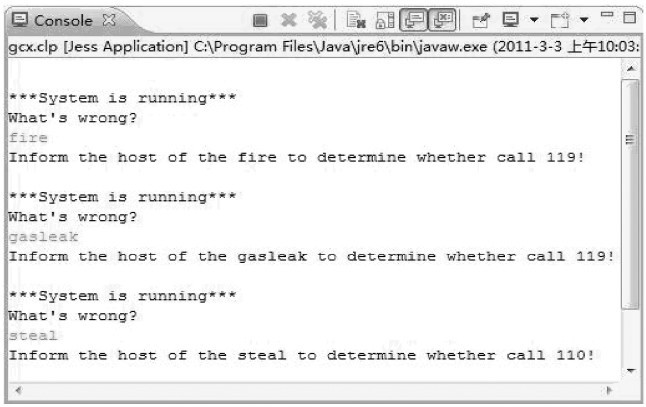
Abstract: According to the development trend of the world smart home security market and security technology, the design of smart home security system based on JESS is proposed. Firstly, the system is researched according to JESS-based expert systems, embedded and wireless sensors. The system consists of access control subsystem, anti-theft alarm subsystem, fire alarm subsystem and gas leakage prevention subsystem. The JESS expert system based on the Java language development rule can judge whether the family status is in a safe state according to the scenes occurring in the family, and timely reflect the non-safe status. The final simulation results verify the design of the system. 0 Preface With the continuous development of society and the increasing income of people, people are paying more and more attention to the safety of living conditions and the reliability of quality of life. The demand for family safety of individual users is growing faster and faster. At the same time, traditional mechanical or security systems that rely solely on human control and operation expose many hidden dangers and deficiencies in actual use, far from meeting people's requirements for smart living; with the popularity of computer technology, Intelligent digital homes are rapidly emerging in people's voices for a better life. As an important part of the security of the entire digital home system, security systems, its reliability, intelligence and security will directly affect the realization of digital home systems. Therefore, this paper proposes a smart home security system based on the JESS expert system. 1 Technical Overview 1.1 JESS and how it works JESS is a rules engine developed by members of the Sandia National Laboratory in the United States in 1995. It is a scripting environment written in the Java language. Its powerful scripting language capabilities provide users with all Java APIs. JESS is small, flexible, and the fastest of known rule engines. JESS adopts production rules as the basic knowledge expression mode, and its core includes fact base, rule base and inference engine. The inference engine is composed of pattern matching, conflict set and execution engine, and the rule base and fact library form a knowledge base. The execution engine activates the rules in the conflict set by a certain priority and modifies the fact store. Loop this process until the fact library has no change and the reasoning ends. The facts include simple facts and object facts. Matching means that JESS operates on fact lines through pattern matching language. The rule base in JESS is a central database that stores the production rules for solving human problem solving in various fields. 1.2 sensor A sensor is a detecting device that can sense the information being measured and can transform the detected information into a device or device that converts the information into an electrical signal or other desired form of information output signal. The types of sensors are very diverse. For example, the gas leakage prevention subsystem uses a gas sensor. When the concentration of gas in the air exceeds the threshold, the signal is sent to the expert system to trigger an alarm. 1.3 Wireless sensing technology The wireless sensor network is composed of a large number of intelligent micro sensor nodes deployed in the monitoring area. The purpose is to cooperatively sense, collect and process the information of the perceived objects in the network coverage area, and send them to the observer or control center, the wireless sensor network. It is wirelessly communicated and requires low-power, short-range wireless communication technology. This article adopts ZigBee technology, which has a very complete protocol hierarchy, featuring low power consumption, low cost, short delay, large network capacity and security, which fully meets the requirements of this system. 2 system architecture 2.1 System characteristics According to the needs of the internal security of the household, the system can be divided into the following subsystems: access control subsystem, anti-theft alarm subsystem, fire alarm subsystem, and gas leakage prevention subsystem. Therefore, the system has the following characteristics: (1) The automaticness of the system Through the corresponding sensors, the system can automatically detect the internal conditions of the home at all times. The access control subsystem can detect the opening and closing of the doors and windows of the whole family; the anti-theft alarm subsystem can detect whether the family has been violently invaded; the anti-fire alarm subsystem can detect fire and smoke; and the anti-gas leakage subsystem can detect the concentration of natural gas in the air. Wait. The specific article only uses the anti-fire alarm subsystem as an example. As usual, when there is an accidental fire, a large amount of smoke will be generated indoors, and a large amount of smoke will be generated at the same time. Therefore, indoor smoke is detected by the smoke detector. The concentration or the detection of the indoor temperature can determine whether there is a fire inside the home, so that the fire can be detected in time, the signal is transmitted to the expert system, and the alarm is transmitted through the expert system, thereby minimizing the loss caused by the fire. (2) System real-time and security The system can respond in real time according to the detected abnormal conditions to ensure the safety of the family and personnel. For example, when the gas leakage prevention subsystem detects that the concentration of natural gas in the air is too high, the natural gas valve is automatically closed and the window can be ventilated in time, and the window is closed after returning to normal. (3) System controllability The working state of the system can be divided into full arming state, half arming state and disarming state. The owner can flexibly configure according to the specific situation. When fully armed, it is suitable for all people in the home. All equipment is armed. The half-armed state can arm a certain protection zone, and is suitable for a state in which a person in the home is asleep or is only active in a single area. Disarmed status: When the disarmed state is applied to someone in the home, all devices are disarmed and all activity information is not collected by the device. This flexible configuration increases system flexibility and avoids false alarms. (4) System's upgradeability The control of the system is controlled by a custom expert system, which is beneficial to upgrade the system. 2.2 System components The system mainly has three functional modules: expert system module, identification module (mainly sensor module), and execution equipment module (including automatic alarm machine, voice circuit, various input and output devices, access control devices, etc.). As shown in Figure 1. Figure 1 System composition The expert system is the "heart" of the entire system, which receives and processes the detected signals, matches the facts according to pre-defined rules, responds in a timely manner, and coordinates the normal operation of each module. The front-end detector mainly refers to the sensor, which is mainly responsible for detecting various parameters (opening and closing of doors and windows, indoor smoke concentration, natural gas concentration, etc.) when an abnormal situation occurs in the detection area, and converting the detected data to actual parameters. Delivered to the expert system via wireless transmission. Input and output devices include keyboards, alarm buzzers, buttons or switches, various types of indicators, and the like. The keyboard is used for inputting and modifying a user password, inputting a phone number for pre-sending a short message notification, and the like. Alarm buzzer and various indicators are used for audible alarms and indications of different operating conditions of the system. Buttons or switches are used for circuit debugging and arming state selection. Voice equipment: mainly used in access control systems. Short message module: mainly sends abnormal conditions to the household through short messages. The wireless communication module is responsible for the information transfer task between the expert system and the sensor. The power supply circuit cooperates with the backup power supply to complete the system power supply in an emergency situation to prevent the security from being out of control due to temporary power failure. 3 Simulation of the experiment 3.1 Reasoning mechanism for discriminating matching rules The expert system of the system uses the JESS rule language to describe the decision rules. The decision rules described by JESS have a unified form consisting of LHS and RHS. The LHS part is composed of different modes, which are used to match the facts in the rule engine, and the RHS part matches the execution action after completion. For example, the LHS part describes the decision rule for judging whether the gas exceeds the threshold, and the RHS part describes actions such as opening the window ventilation, issuing an alarm signal, and notifying the owner of the message. For the same decision rule, only if all the modes in the LHS match the facts (that is, the signals transmitted by the sensor), the rule can be activated and the RHS action can be executed. According to the above description, when the system receives the decision request, the execution flow of the decision rule in the rule engine is described as follows: When the expert system receives the request signal transmitted by the detection device, the rule engine destroys automatically generates a refact fact in the decision fact buffer. If the fact of the refact matches the Nth pattern nfact in the mapping rule, the mapping rule is activated. The RHS action of the mapping rule nfact is executed, and the execution instruction is transmitted to the execution device. 3.2 Logical representation and reasoning In the system, the implementation of the rules requires corresponding context support. For example: "When the expert system receives the trigger signal transmitted by the identification device, the expert system converts the signal into ("What?") based on the information and knowledge base in the database, and then transmits the resulting "problem" to Matching facts in the rules engine: (1) Identifying the device (trigger signal) ∧ controlling the device (receiving the signal); (2) control device (execution), control device (transmitting information to control device), identification module (receiving information); (3) Identification equipment (identification information, database and knowledge base), control equipment (information for detection and identification); (4) Control device (information) ∧ Execution device (test result, execute command) The above process can also be expressed using the following formula: i∈I,c,Cr ∈C,e∈Ee,d ∈D,k∈K[identify(i)∧pass(i,c)∧judge(c)∧pass(c,i) ∧compose(i,d,k)∧result((i,d,k),r)∧pass(r,Cr)∧judge(Cr)→execution(e)] 3.3 Verification of the rule execution mechanism Experimental scenario: The experimental scenario includes a fire protection subsystem, an anti-theft subsystem, and an anti-natural gas subsystem. When the responding sensor receives the sensor's "abnormal detection signal", the signal is immediately transmitted to the expert system, and the expert system responds according to pre-set rules. Experimental data: The data described in the experiment mainly includes two types, one is the declaration of basic facts (simulation of the normal situation of various data inside the family), and the other is various rules (decision rules and mapping rules) The definition of the definition and judgment of the critical value of various emergencies is limited to the length of the paper. This paper has done the most simplification, and only gives the basic facts and judgment rules to simulate real life. Experimental environment: a PC (2.26GHz CPU, 2GB memory), operating system Microsoft Windows 7, rule engine JESS (Ver 7.1p4) and so on. Experimental purpose: Through the above experiments, the abstract execution flow of the above decision rules is demonstrated, and the simulation system is used to prove that the expert system is reliable. Analysis of experimental results: In this experiment, in order to facilitate the understanding of the experimental process, in the processing of experimental data files, whether it is to declare facts, or to define rules, etc., this article has done the most to simplify, only use key concepts to assert facts (ie the various emergencies of the simulation). Experiments with complex conditions can be done on this basis by adding various detailed assertions. This experiment is only a simulation, but according to the description of the application scenario, the experimental results are correct, and the validity of the decision rule is verified according to the predetermined judgment, which proves that the execution flow of the decision rule designed in this paper is implementable. The output is shown in Figure 2. Figure 2 output 4 Conclusion    Based on the JESS expert system, the smart home security system uses the control technology to realize the functions of indoor comprehensive, three-dimensional, perfect fire detection, door and window anti-smashing, anti-gas leakage and other intelligent security alarm automation, high reliability and simple use. Low cost, able to meet the general needs of the family. The system makes full use of the advantages of communication within the local area network, realizes the functions of rapid alarm and real-time detection, and can also upgrade the system and integrate new functional modules to meet the future development of smart home. Therefore, with the development of wireless communication technology and Internet technology, the system can also be used in places where security, such as banks, libraries, large supermarkets, etc., is extremely widely used, and is developable and expandable.
Quick Couplings can be divided into two types of male and female, the following will be introduced to the B, C, D, DC four models are female (with the ear), A, E, F, DP is the male No ear). Use for water,oil,gas,etc.
Materials: Stainless Steel, Aluminium, Brass
Type: A,B,C,D,E,F,DC,DP
Finishing: Original and Maching
Size: 1/2" to 4"
Threads: BS, NPT, DIN
Camlock Couplings,Stainless Steel Camlock Coupling,Brass Couplings,Camlock Quick Coupling HEBEI ZIFENG NEW ENERGY TECHNOLOGY CO.,LTD. , http://www.zifengpipeline.com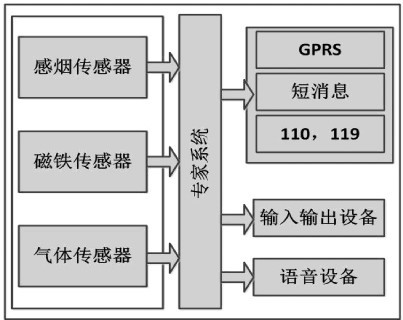

0 times
Window._bd_share_config = { "common": { "bdSnsKey": {}, "bdText": "", "bdMini": "2", "bdMiniList": false, "bdPic": "", "bdStyle": " 0", "bdSize": "24" }, "share": {}, "image": { "viewList": ["qzone", "tsina", "tqq", "renren", "weixin"], "viewText": "Share to:", "viewSize": "16" }, "selectShare": { "bdContainerClass": null, "bdSelectMiniList": ["qzone", "tsina", "tqq", "renren" , "weixin"] } }; with (document) 0[(getElementsByTagName('head')[0] || body).appendChild(createElement('script')).src = 'http://bdimg.share. Baidu.com/static/api/js/share.js?v=89860593.js?cdnversion=' + ~(-new Date() / 36e5)];